With more and more things becoming digital, it is important for businesses to secure their information. However, this sounds easier than it actually is. Some companies do not have the resources to keep a constant eye on their security and look for potential threats or weaknesses. Another issue is that security and their systems are becoming more complex. Without this complexity, there would be holes in the security that would allow for vulnerabilities. Konica Minolta has years of experience and can evaluate areas where security is important and relevant. Konica Minolta can offer the right security solutions and services for IT security, data security, multifunctional system security and intelligent video solutions security.
Focusing only on network and IT security can leave you open to potential security gaps and threats. Different devices that are used every day, such as a tablet in the field, all have the potential to be an attack point. Another thing that happens is that while they are equipped correctly, they do not use the security solutions properly or they do not have policies in place. Konica Minolta frequently encounters a lack of network access controls or passwords that are adequate, which leaves the business vulnerable. Furthermore, certain aspects can be neglected, which can leave important data on hard drives or solid state drives at risk. Forrester Research found out that two thirds of companies have had a data breach due to a vulnerability in hardware security. Lastly, the employees play a key part in security as well. Having well informed employees who can detect a social engineering attack, which works by having the employee click on a malicious link in an email.

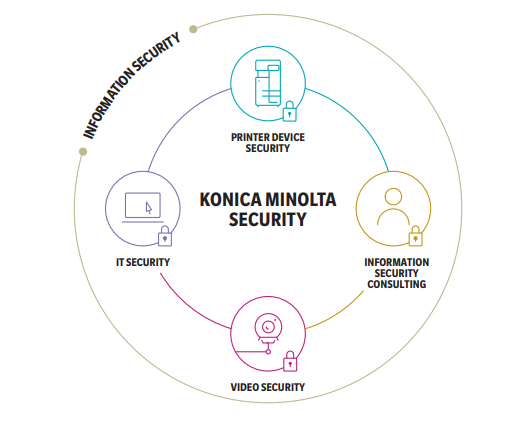
Konica Minolta uses 360-Degree Strategy to provide comprehensive security. To achieve this, Konica Minolta looks at printer device security, IT security, video security, and through information security consulting. This approach is based on the premise that if you only focus on one or two of the areas, that there will still be areas of vulnerability.

Multifunctional printers (MFPs) are more than just a printer or copier and have to have proper security to protect that information and data that goes through the MFP or is stored on it. Bizhub SECURE works to cover three areas, which include access control and access security, storage media data security and network security. One aspect that is important is that while these security measures should provide protection, it should never come at the expense of usability. This is not because it might slow down productivity, but because if the users view the security measures as a hinder to them, they are less likely to comply and follow them. Bizhub SECURE Alert and LK-116 BitDefender® Virus Scan Functions are things that Konica Minolta offer as security measures to help protect MFPs.

IT security begins with evaluating risks. Analysis of risks and having contingency plans increase the awareness of risk, while also reducing the chance of possible damage. Deloitte did a study and found that 58% of companies have an emergency plan. Konica Minolta has almost 20 years of experience and uses this when evil sting business and finding what each individual business’ needs are and then create specific security measures in a detailed plan for the business.

Video security can be used by a business to protect valuable information. The first step is deciding what needs to be seen, like the door to file cabinets or entrances. The business’ network is considered because the network has to be able to handle the high-resolution recordings that the video security will use. Next the decision has to be made if the video security system will be added on to an existing network or will have a separate network installed. Additionally, data protection is considered when adding a video security system. How long the data is stored is one question that needs to be considered.

Information security consulting is the last part of the 360-degree strategy. Information security is important in protecting data and to a business’ success, while also being required by law due to legal regulations. Appropriate analysis is important when determining what type of protections they need. Employee training is key to emphasizing the importance of information security. One area of information security is access security. This is who can access certain data. The more important or sensitive the data is, the more restrictive the group who has access to it should be. Additionally, when storing data, it should be encrypted so there is additional security on top of a password. The same is true for transporting data. Lastly, if violations occur, protocol data and logs should be available so they can be identified and to check for damage concerns.
All of us who live in this interconnected world are familiar with the password polka. We have files or black books filled with the myriad passwords required for our activities from banking to fulfilling our pets’ medications. We attempt to log into sites which have inevitably required a password change two weeks ago. We try to change our passwords per the requirements of our benevolent policy overlords only to discover that we have already used that password, or we are required to use the special characters !@#&@ and one UPPERCASE.
!@$& is right.
One of the biggest frustrations we experience as both consumers and IT professionals has to do with this !@$&-ing dance. In fact, according to the Gartner Group, password resets consume 30% of all IT call volume. And at an estimated 25$ per call (Gartner estimates this amount to be higher at $70 per call) with an average of 1.75 calls per month per person (META Group), this places the cost to a company of 50 employees for password resets alone to nearly $8,000!
And this is where the frustration for the benevolent policy overlords begins. An aggressive password reset policy will undoubtedly increase this number, but $8,000 is small price to pay for the risk mitigation that comes with strong password rules. In fact the risk of exposure, data loss or other more nefarious problems is more or less limitless.
Using this logic, we as IT administrators should increase the strength of our password policies and consider the cost on the support end just the cost of doing business. I have personally run into sys admins who require insanely complex passwords that reset on very short schedules. These security minded individuals believe that the cost of a breach is so severe that end user frustration and support costs are not worthy of consideration.
–And, they would be right…If it weren’t for a couple of big problems.
The first that we incorrectly assess password strength based on our own fleshy weaknesses. Consider the following “complex” password: 1Dr@g0n!
This passes some of the most complex rule systems out there, but could be cracked by a bot running on a low-grade PC in about 3 days…more sophisticated attacks would demolish this password.
This problem is summed up beautifully by the folks at xkcd.com (a wonderfully nerdy web comic).
The other problem with using what we consider to be complex password policies is, as the comic so elegantly shows: we forget them. And when we forget them, we put them in our little black book, save them in a password file…with a password, probably, or simply write them down on a sticky and put it under our keyboard or on our monitor.
The last offense is obviously an unacceptable breach of password protection, but the sys admin would have no one to blame but herself. She created a password policy that broke the end-user thus leaving a huge hole in their security.
How do we get around this as both consumers and IT professionals? Well, here are a few suggestions:
There are many other authentication solutions to fit many applications, but they don’t all belong in the conversation about our some-time friend the password, so please forgive me if I have left your favorites out of the list. I hope this helps all of you dancing the password polka!